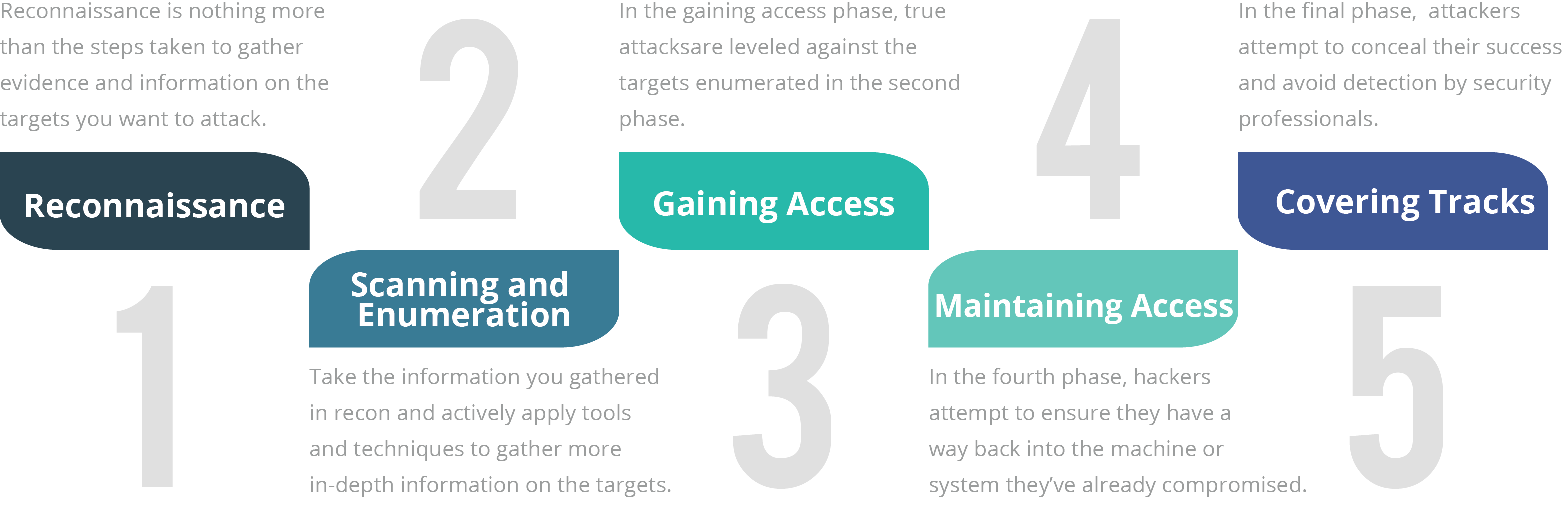
Although there are many different terms for these phases and some of them run concurrently and continuously throughout a test, EC-Council has defined the standard hack as having five phases. Whether the attacker is ethical or malicious, these five phases capture the full breadth of the attack.